Struggling with multiple programming languages? No worries. Our Code Converter has got you covered. Give it a go!
It goes without saying that vulnerability testing is one of the most important security measures organizations must take to protect their networks, data, and applications. Statistically, it is expected that cybercrime will cost organizations worldwide around $10,5 trillion every year by 2025. Sounds terrible, right?
Therefore, it is essential to understand different types of vulnerabilities and the proper methods to detect and address them. This comprehensive guide to non-intrusive vulnerability assessment provides an overview of the different tools, techniques, and processes used to identify and fix security flaws. It outlines the steps needed to identify and address vulnerabilities, as well as the most common techniques used to detect them. To top it up, we'll provide recommendations for improving security practices and reducing the risk of exploitation. So, run over it and ensure that your data is protected from malicious actors.
Table of contents:
- Types of Vulnerabilities
- Vulnerability Assessment Process
- Common Vulnerability Detection Tools
- Network Vulnerability Scanning
- Application Vulnerability Scanning
- How Python is Involved
- Conclusion
Types of Vulnerabilities
You have to bear in mind that there are three types of vulnerabilities that need to be addressed during the vulnerability testing process: software, network, and configuration/product. Software vulnerabilities affect the program code and could result in a system crash or remote code execution. The most common types of software vulnerabilities are:
- Authentication: Authentication vulnerabilities allow attackers to gain access to systems or data without proper authorization. Examples include weak user passwords and default account passwords.
- Authorization: Authorization issues occur when the system allows users to access more data or functionality than they should have. For example, access control lists (ACLs) are not properly configured.
- Client-side: These vulnerabilities are found on the computer or device that is accessing the network or system. An example is when a system downloads unverified or malicious code, such as a virus or worm.
- Configuration (misconfiguration): Configuration vulnerabilities occur when a system is not configured correctly. Examples include default settings that are not changed.
- Data (integrity and availability): Data vulnerabilities could result in the data being accessed, altered, or destroyed. Examples include data being read, deleted, or modified by unauthorized users.
- Denial of Service: Denial-of-Service (DoS) vulnerabilities are aimed at causing the system to crash or be unavailable to users (there are many types of DoS attacks, such as SYN Flooding, UDP flooding, ICMP, and more).
- Escalation of privilege: This type of vulnerability is aimed at allowing an attacker to gain elevated privileges on the system.
- Information disclosure: This type of vulnerability occurs when sensitive information is sent unencrypted and could be accessed by unauthorized individuals.
- Resource consumption: Resource consumption vulnerabilities occur when an application needs more system resources than it should, potentially crashing the computer.
Vulnerability Assessment Process
The first step in conducting a vulnerability assessment is selecting the right scanning tool or combination of tools based on the environment, assets, and use cases. Depending on the type of scan and the organization’s needs, the tools could include vulnerability scanners, security assessment tools, or network scanners.
Once the tools are selected, organizations should first identify the assets they want to scan and the networks they need to examine. The next step is to prioritize the assets based on criticality and then create a scanning schedule. Once the scan is complete, it is time to review the results and create a report.
The report should include a list of vulnerabilities identified, severity level, mitigation recommendations, and other details, such as assets scanned, network ports scanned, and operating system used for the scans. The last step is to create a remediation plan. This plan should include the prioritization of the vulnerabilities based on their criticality level and the recommended mitigation actions.
Common Vulnerability Detection Tools
There are various tools and services available to organizations for conducting vulnerability scans. Many of these tools are categorized as either automated or manual vulnerability scanners.
- Automated vulnerability scanners - These scanners use program logic and algorithms to scan networks, systems, and applications for vulnerabilities. They can be programmed to scan specific assets, IP addresses, ports, or operating systems. They also have the ability to scan all assets, as well as be set to high-risk items or host-based rules. Some automated vulnerability scanners can also scan through firewalls.
- Manual vulnerability scanners - These tools provide organizations with a manual option for scanning their networks, systems, and applications for vulnerabilities. They allow security teams to test the security of their applications and systems, identifying any potential problems.
- Network vulnerability scanners - These tools are designed to scan networks and identify any potential vulnerabilities. They are typically used to identify what hosts are connected to the network, what services are available, and what ports are open.
- Application vulnerability scanners - These tools help identify any potential vulnerabilities in applications. They are often used for testing a single application, such as an application running on the internet, or a group of applications, such as web applications.
- Configuration and risk assessment tools - These tools combine network and application vulnerability scanners. They are typically used by security teams to test multiple aspects of the network, such as the internet, web applications, email servers, databases, and virtual private networks (VPNs).
Network Vulnerability Scanning
Network vulnerability scanning is the process of identifying potential security issues and weaknesses on a network. It involves scanning a network to identify hosts, services, open ports, network configuration, and other vulnerabilities. Network vulnerability scanners are often used to identify misconfigurations of hosts or services, as well as open ports that could be used for malicious purposes. This process typically uses two different scanning techniques:
- Ping scanning - This technique sends ICMP echo request packets to hosts on the network, and if there is no response, then the host is considered offline. If a host responds, the scanner logs the host’s IP address, hostname, operating system, and open ports.
- TCP/UDP port scanning - This technique sends TCP or UDP packets to a network or host and records any response. If there is no response, then the port is assumed to have a closed state. If there is a response, the scanner logs the open port, the service that is running on the port, and the protocol being used.
Application Vulnerability Scanning
It is the process of testing applications for potential vulnerabilities. Its main goal is to identify issues such as missing patches, incorrectly configured settings, and potential flaws in the code. It is important to test applications after deploying them to ensure there are no issues. Organizations can use automated or manual scanners to do this. Manual scanners require the tester to execute the application and then identify any issues. This method is good for testing single applications, but it is not very scalable. Automated scanners, on the other hand, are scalable and can scan multiple applications at the same time.
How Python is Involved
There are several ways you can add a Python touch to your vulnerability assessment process. Here are a few examples:
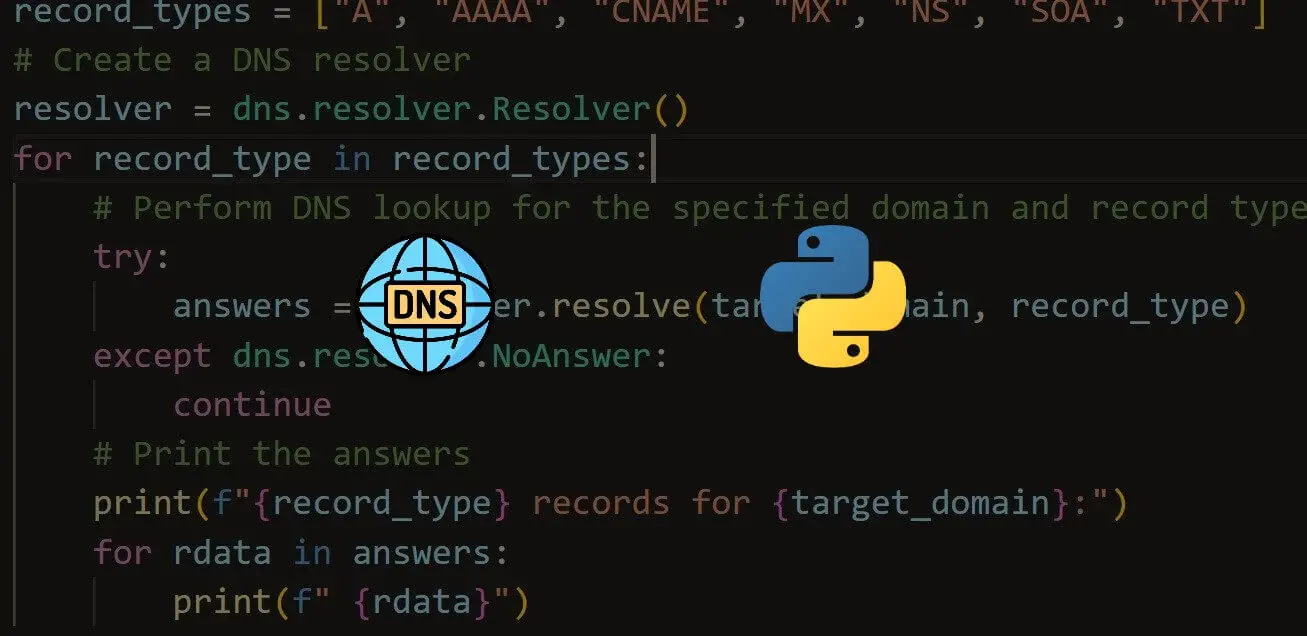
- Using Python libraries to perform vulnerability scans: There are several Python libraries available that can help you perform vulnerability scans on your network or application. Some popular ones include Nmap, Scapy, and Python-nmap. These libraries can be used to perform network scans, port scans, and service detection on your assets.
- Automating the vulnerability assessment process: You can use Python to automate various tasks involved in the vulnerability assessment process, such as scheduling scans, generating reports, and sending notifications. This can help you save time and improve efficiency.
- Developing custom scripts to identify specific vulnerabilities: Python is a versatile language that can be used to develop custom scripts to identify specific vulnerabilities. For example, you can use Python to write scripts that check for weak passwords, misconfigurations, or known vulnerabilities in your systems.
- Use Machine Learning models to detect vulnerabilities: You can use Python to train machine learning models that can detect vulnerabilities in your systems. For example, using supervised learning techniques like Random Forest, you can train a model to identify patterns in your network traffic that indicate a potential vulnerability.
- Integrate with other tools: You can use Python to integrate your vulnerability assessment process with other tools, such as vulnerability management platforms, incident response systems, and security information and event management (SIEM) tools. This allows you to gain a more complete view of your security posture and respond to threats more effectively.
Conclusion
Vulnerability testing is an important security measure that could help organizations avoid a breach. It is essential for business owners to understand the different types of vulnerabilities and the most effective methods to detect and deal with them. Overall, we can see that vulnerability testing is a critical part of any security strategy. It helps identify weak points in the network, allowing organizations to take steps to address them before they become a problem. With the rise of new technologies and the ever-changing cyber threat landscape, non-intrusive vulnerability testing has become an increasingly important tool.
Are you interested in learning more about ethical hacking and building tools to protect against cyber threats? Our Ethical Hacking with Python Ebook is the perfect resource for you! This comprehensive guide covers building tools in various topics, including information gathering, malware, and network packet manipulation. You'll learn how to build tools like a reverse shell, password cracking tools, and many more (More than 35 pen-testing tools).
With step-by-step instructions and clear explanations, this EBook is perfect for both beginners and experienced professionals looking to expand their knowledge in the field of ethical hacking with Python. Don't miss out on this opportunity to become an expert in cyber security – get your copy today!
Happy hacking ♥
Finished reading? Keep the learning going with our AI-powered Code Explainer. Try it now!
Got a coding query or need some guidance before you comment? Check out this Python Code Assistant for expert advice and handy tips. It's like having a coding tutor right in your fingertips!