Want to code faster? Our Python Code Generator lets you create Python scripts with just a few clicks. Try it now!
Have you ever wondered how your laptop or mobile phone knows which wireless networks are available nearby? It is actually straightforward. Wireless Access Points continually send beacon frames to all nearby wireless devices; these frames include information about the access point, such as the SSID (name), type of encryption, MAC address, etc.
In this tutorial, you will learn how to send beacon frames into the air using the Scapy library in Python to forge fake access points successfully!
Necessary packages to install for this tutorial:
$ pip3 install faker scapyTo ensure Scapy is installed properly, head to this tutorial or check the official scapy documentation for complete installation for all environments.
It is highly suggested that you follow along with the Kali Linux environment, as it provides the pre-installed utilities we need in this tutorial.
Before we dive into the exciting code, you need to enable monitor mode in your network interface card:
- You need to make sure you're in a Unix-based system.
- Install the aircrack-ng utility:
$ apt-get install aircrack-ngNote: The aircrack-ng utility comes pre-installed with Kali Linux, so you shouldn't run this command if you're on Kali.
- Enable monitor mode using the airmon-ng command:
root@rockikz:~# airmon-ng check kill
Killing these processes:
PID Name
735 wpa_supplicant
root@rockikz:~# airmon-ng start wlan0
PHY Interface Driver Chipset
phy0 wlan0 ath9k_htc Atheros Communications, Inc. TP-Link TL-WN821N v3 / TL-WN822N v2 802.11n [Atheros AR7010+AR9287]
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)Note: My USB WLAN stick is named wlan0 in my case, you should run the ifconfig command and see your proper network interface name.
Alright, now you have everything set, let's start with a simple recipe first:
from scapy.all import *
# interface to use to send beacon frames, must be in monitor mode
iface = "wlan0mon"
# generate a random MAC address (built-in in scapy)
sender_mac = RandMAC()
# SSID (name of access point)
ssid = "Test"
# 802.11 frame
dot11 = Dot11(type=0, subtype=8, addr1="ff:ff:ff:ff:ff:ff", addr2=sender_mac, addr3=sender_mac)
# beacon layer
beacon = Dot11Beacon()
# putting ssid in the frame
essid = Dot11Elt(ID="SSID", info=ssid, len=len(ssid))
# stack all the layers and add a RadioTap
frame = RadioTap()/dot11/beacon/essid
# send the frame in layer 2 every 100 milliseconds forever
# using the `iface` interface
sendp(frame, inter=0.1, iface=iface, loop=1)Related: Build 24 Ethical Hacking Scripts & Tools with Python Book
The above code does the following:
We generate a random MAC address, set the name of the access point we want to create, and then create an 802.11 frame. The fields are:
- type=0: indicates that it is a management frame.
- subtype=8: indicates that this management frame is a beacon frame.
- addr1: refers to the destination MAC address, in other words, the receiver's MAC address. We use the broadcast address here ("ff:ff:ff:ff:ff:ff"). If you want this fake access point to appear only on a target device, you can use the target's MAC address.
- addr2: source MAC address, the sender's MAC address.
- addr3: the MAC address of the access point.
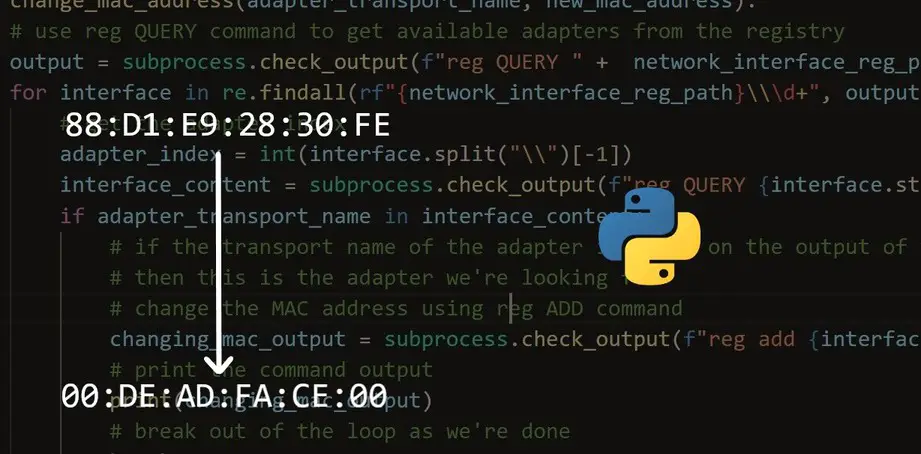
Related: How to Make a MAC Address Changer in Python
So we should use the same MAC address of addr2 and addr3 because the sender is the access point!
We create our beacon frame with SSID Infos, then stack them all together and send them using Scapy's sendp() function.
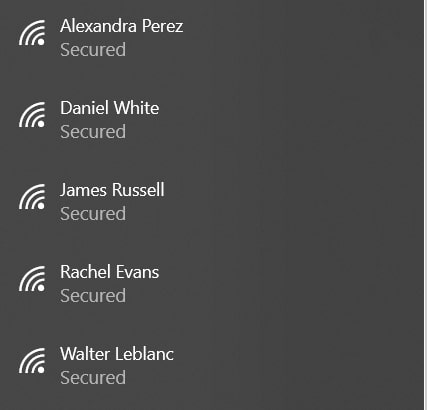
After we set up our interface into monitor mode and execute the script, we should see something like that in the list of available Wi-Fi access points:

Now let's get a little bit fancier and create many fake access points at the same time:
from scapy.all import *
from threading import Thread
from faker import Faker
def send_beacon(ssid, mac, infinite=True):
dot11 = Dot11(type=0, subtype=8, addr1="ff:ff:ff:ff:ff:ff", addr2=mac, addr3=mac)
# ESS+privacy to appear as secured on some devices
beacon = Dot11Beacon(cap="ESS+privacy")
essid = Dot11Elt(ID="SSID", info=ssid, len=len(ssid))
frame = RadioTap()/dot11/beacon/essid
sendp(frame, inter=0.1, loop=1, iface=iface, verbose=0)
if __name__ == "__main__":
# number of access points
n_ap = 5
iface = "wlan0mon"
# generate random SSIDs and MACs
faker = Faker()
ssids_macs = [ (faker.name(), faker.mac_address()) for i in range(n_ap) ]
for ssid, mac in ssids_macs:
Thread(target=send_beacon, args=(ssid, mac)).start()
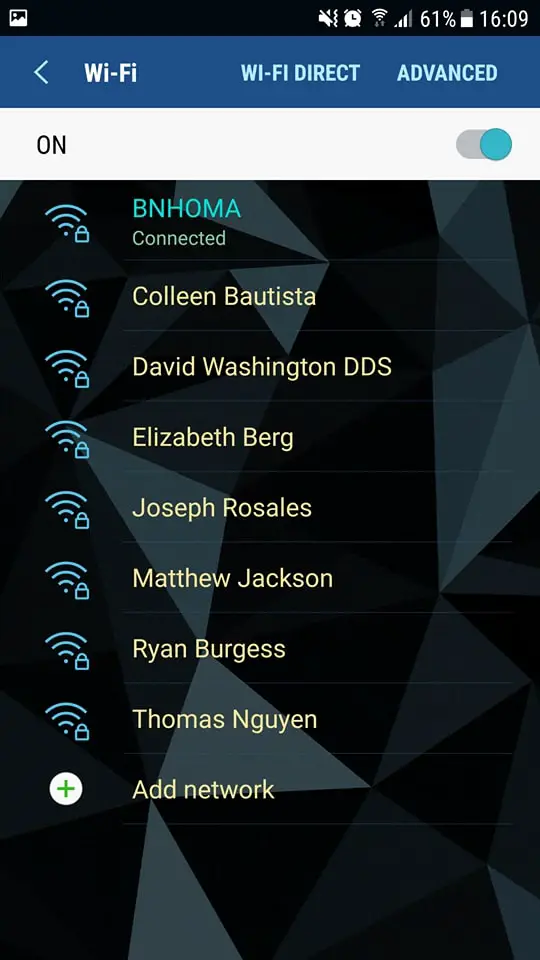
All I did here was wrap the previous lines of code in a function, generate random MAC addresses and SSIDs using the faker package, and then start a separate thread for each access point. Once you execute the script, the interface will send five beacons each 100 milliseconds (at least in theory). This will result in appearing of five fake access points. Check this out:
Here is how it looks on Android OS:
If you're unsure how to use threads, check this tutorial.
That is amazing. Note that connecting to one of these access points will fail, as they are not real access points, just an illusion!
Finally, we have an Ethical Hacking with Python Ebook, where we build 24 hacking tools and scripts! Make sure to check it out if you're interested.
RELATED: How to Make a DNS Spoof attack using Scapy in Python.
Alright, that's it, Happy Crafting ♥
Just finished the article? Why not take your Python skills a notch higher with our Python Code Assistant? Check it out!
View Full Code Understand My Code

Got a coding query or need some guidance before you comment? Check out this Python Code Assistant for expert advice and handy tips. It's like having a coding tutor right in your fingertips!